security
Use an Authenticator App to Login to PayPal
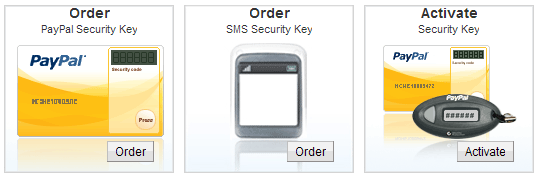
PayPal seem to think that SMS text messages are a secure two-factor authentication method. Sadly, they are greatly mistaken. This article explains why and what to do about it.
How to create secure certificates

Generate certificates for Node-RED that are trusted by all modern browsers. This will let you access Node-RED (and other services) over an encrypted HTTPS link.
How to secure Node-RED

Node-RED is increasingly used in situations that require reasonable security. Up to now, however, the information required to secure it correctly has been fragmented. This article aims to give an end-to-end outline to enable anyone to secure their installation.
📖 Posts | 📎 Blogging, Development | 🔖 Security, security threats, threat management, vulnerabilities, Web
Cloudflare Now Active
After the recent high-profile vulnerabilities, I decided to turn on the free version of CloudFlare for this domain. CloudFlare provides a reverse proxy service that sits in front of your domain. It will serve content where it can on your behalf (caching), optimise content where it can (e.g. minimising JavaScript, HTML, CSS, etc.). But even more important from my perspective is their ability to protect against a number of vulnerabilities.
📖 Posts | 📎 Enterprise, IT Security, Microsoft | 🔖 cyber security, Enterprise Architecture, Enterprise Systems, Governance, government, Microsoft, nhs, Office 365, Presentation, Security, Solutions Architecture
Presentation: Security and Governance in the Cloud
Here is a presentation that I did recently for NHS CIO’s and CCIO’s. It is all about how NHS England has followed a journey to cloud services and the IT Security & Information Governance issues we had to deal with along the way. It tries to also show other NHS organisations how they might work towards similar aims.
📖 Posts | 📎 General | 🔖 anti virus, cyber security, Enterprise Systems, patching, Security, security threats, software, threat management, vulnerabilities, whitelisting
Stay Secure! The Latest Recommendations for IT Security
Individuals and enterprises do not understand the value of their Information nor how to protect it. This article attempts to reveal simple and practical ways to protect IT assets and outlines some of the latest thinking and tools from industry experts.
Keeping information secure but accessible across platforms
One of the issues with Linux is that I can’t use it under all circumstances. In particular I usually have to work with Windows at work. So I need cross-platform tools, especially now that I also make extensive use of a smartphone/PDA. So here is a timely post – with the number of people in UK government departments carelessly loosing private or secret information, how do we keep this stuff secure while still being accessible from different platforms?
Update on FreeOTFE
Thought I would add a quick update on using FreeOTFE under Windows and PocketPC. I tried it under Windows on a different PC and it does indeed work OK though it is nowhere near as polished as TrueCrypt. I’ve also tried again a few times on a PocketPC with limited success and I think I know what is happening. Firstly, you must install FreeOTFE for PPC into system memory and not on a storage card – not terribly surprising really.


